When designing from zero to one (0-to-1), UX practitioners face a common dilemma: How do you create something entirely new when users can’t articulate what they need, timelines are compressed, and the stakes are extraordinarily high? In cybersecurity—specifically identity security—this challenge intensifies. Unlike consumer products, in which users might tolerate minor friction, security products demand precision, clarity, and unwavering trust. A confusing interface can delay critical incident response to a cyber attack. An unclear workflow can result in misconfigured permissions, leaving an enterprise vulnerable to compromise. A poorly designed alert system can cause alert fatigue, leading admins to miss genuine threats.
Identity security amplifies these challenges exponentially: Enterprises manage hundreds or thousands of identities—human users, service accounts, and applications—and each has complex permission structures across cloud and on-premises systems, which creates vast attack surfaces that administrators must monitor and protect with limited time and resources. This case study chronicles our journey in designing a brand-new identity security product from scratch while navigating limited domain knowledge, unclear user personas, and tight timelines in a space where minor UX missteps could have high-stakes consequences. Through the process of designing an effective product, we crafted a new framework for how admins perceive and act on risk. For UX teams working in 0-to-1 spaces within high-risk domains, our story offers hard-won insights about designing for trust, urgency, and clarity when the margin for error is slim.
Understanding Identity Security
The term identities encompasses any entity that can access organizational systems and data, including human users, service accounts, applications, and automated processes. The scale and stakes are substantial: Enterprises manage thousands of identities across complex environments, and the majority of security breaches involve compromised credentials or identity-based attacks. When an identity is compromised or misconfigured, it’s akin to handing attackers the keys to your entire digital infrastructure, which is why identity-related breaches rank among the costliest security incidents organizations face. Identity and Access Management (IAM) administrators face the daunting task of visualizing complex permission structures across hundreds of systems, detecting anomalies among thousands of events daily, and remediating risks before they escalate—all with limited time and resources. This is why intuitive design isn’t a luxury in identity security; it’s a critical defense mechanism.
The Market Gap
Although existing identity security tools excel at detection, they fragment the administrator experience across multiple systems, requiring users to manually correlate alerts, assess risk context, and determine remediation steps across disconnected interfaces. These solutions generate exhaustive data but provide little guidance on prioritization, leaving IAM admins overwhelmed by alerts without clear pathways to resolution. The market lacks a unified solution that can identify identity risks and confidently take action to resolve them.
Our Challenge
We aimed to design a standalone identity security product that would protect organizations from identity-based attacks while providing unprecedented visibility into risk.
However, as we set out on this journey, we faced significant challenges:
- limited domain knowledge of identity security within our design and product teams, as our current product was designed for a different set of IT personas and workflows
- unclear user personas spanning technical admins to executive decision-makers
- ambiguous workflows around risk remediation and identity management
- tight timelines with high executive visibility
- complex technical constraints around existing product architecture
The stakes were clear: We needed to move fast without compromising quality, trust, or usability.
Design Process: From Ambiguity to Clarity
We worked through five phases over 20 weeks. Rather than following a linear path, we moved fluidly between phases, brought stakeholders into key decisions, tested assumptions continuously, and made strategic trade-offs that protected user value.
Table 1: Design Process Overview
| Phase | Timeline | Key Activities | Challenges | Deliverables |
| Phase 1: Discovery | Weeks 1-3 | • Market opportunity identification • Initial stakeholder alignment • Problem space exploration • Competitive landscape review | • Limited domain knowledge • Unclear user personas • Ambiguous workflows • Tight timelines with high visibility | • Problem statement • Initial opportunity brief • Stakeholder alignment • Research plan |
| Phase 2: Research | Weeks 3-6 | • Semi-structured interviews (n = 15) • Contextual inquiry (n = 8) • Competitive analysis (8 solutions) | • Access to target users • Balancing depth versus speed • Synthesizing complex domain knowledge • Defining diverse personas | • Four primary personas defined • Key insight documentation • Mental model maps • User journey maps • Competitive analysis report |
| Phase 3: Ideation and Alignment | Weeks 6-8 | • Co-design workshop • User story prioritization • Architectural decision-making • Concept design • Executive presentation | • Balancing user needs versus technical constraints • Aligning cross-functional teams • Defending architectural decisions • Scope definition | • MVP scope definition • Architecture and navigation flows • Identity summary page concept • Executive sign-off |
| Phase 4: Design and Iteration | Weeks 8-14 | • Design principles establishment • Rapid prototyping • Information architecture design • Design iterations • Cross-team design critiques • Usability testing (n = 12) | • Ensuring differentiation • Managing executive pressure • Incorporating feedback quickly | • Design system components • Purpose-built identity and access (IA) • Interactive prototypes • Usability test findings • Refined designs |
| Phase 5: Delivery and Scoping | Weeks 16-20 | • Strategic de-scoping (P0/P1/P2) • Onboarding flow design • Design handoff • Developer collaboration • Launch and GTM preparation | • Balancing speed with quality • Protecting core experience • Managing scope creep • Maintaining design intent | • Prioritized feature list • Onboarding flows • Design specifications • Component documentation • Launch-ready product |
Phase 1-2: Discovery and Research (Weeks 1-6)
To ground our design decisions in real user needs, we embarked on a comprehensive research initiative spanning multiple methodologies.
We employed these research methods:
- Semi-structured interviews (n = 15): IAM administrators, security engineers, and IT managers helped us understand current workflows, pain points, and decision-making processes.
- Contextual inquiry (n = 8): Shadowing admins during actual risk investigation and remediation let us capture daily tasks, challenges, and time spent on identity-related activities over 2 weeks.
- Competitive analysis: We evaluated eight competing solutions to identify gaps and opportunities.
- Internal stakeholder workshops: Cross-functional teams aligned on user stories and MVP scope.
The research helped us understand how they approached identity risk and threat resolution. The key goals for our user research were to gather requirements and build deep empathy with users navigating complex, high-stakes workflows in which mistakes could be catastrophic. These sessions revealed critical insights that would become the foundation of every design decision.
Table 2: Core User Insights from Foundational Research
| Finding Category | Key Insight | Design Implication |
| Timeline Expectations | Risk remediation often takes weeks, not days. | Design for long-term tracking and progressive workflows, not just immediate actions. |
| Organizational Dynamics | IAM and security operations teams have distinct but intersecting workflows. | Create flexible views supporting different role-based perspectives. |
| Decision-Making Criteria | Admins prioritize criticality versus complexity when tackling policy violations. | Build intelligent prioritization that balances risk severity with remediation effort. |
| Tool Fragmentation | Visibility across alerts, roles, and recovery timelines is fragmented and frustrating. | Unify information architecture in a single, comprehensive view. |
| Cognitive Load | Admins manage 50-200+ identities with varying risk levels. | Implement progressive disclosure and smart filtering. |
| Trust and Validation | Users need to verify recommendations before taking action. | Show clear evidence and impact analysis before remediation. |
We also identified and defined multiple personas, clarifying that our primary users were IAM admins, with secondary influencers in security and IT leadership. Understanding these distinct personas was crucial to creating a product that served both operational and strategic needs.
Table 3: Primary Personas and Their Needs
| Persona | Primary Goals | Key Pain Points | Design Focus |
| IAM Administrator (Primary) | • Quickly identify high-risk identities. • Remediate violations efficiently. • Prove compliance. | • Too many alerts • Unclear prioritization • Limited context for decisions | Daily operations, workflow efficiency, and clear remediation paths |
| Security-Ops Engineer | • Detect identity-based attacks. • Understand blast radius. • Coordinate response. | • Fragmented tools • Slow investigation • Poor team visibility | Threat investigation, data correlation, and collaboration features |
| CISO | • Understand risk posture. • Justify security investments. • Report to the board. | • Lack of executive visibility • Difficulty quantifying ROI • Complex technical reports | Strategic overview, executive dashboards, and clear risk metrics |
| IT-Ops Manager | • Maintain system availability. • Minimize business disruption. • Balance security and productivity. | • Disruptive remediation tasks • Unclear business impact • Resource constraints | Change management, impact assessment, and resource planning |
This research phase clarified that our primary users—IAM admins—were primarily struggling with fragmented tools that detected risks but provided little guidance on prioritization or remediation.
Phase 3: Ideation and Alignment (Weeks 6-8)
To accelerate clarity, the design team facilitated intensive in-person workshops with all key stakeholders from product, sales, growth, and marketing teams to help scope the MVP for this extremely ambitious product. The goal was to balance time-to-market with delivering a product that was truly valuable to users. As a team, we leveraged insights from the discovery phase to help create and prioritize user stories. For example, the insight that “visibility across alerts, roles, and recovery timelines was fragmented” directly generated our highest-priority user story: “As an IAM admin, I need a unified view of each identity’s risk profile so I can quickly assess and act on threats.”
Meanwhile, the finding that “users need to verify recommendations before taking action” elevated impact analysis features from P1 to P0 status. We couldn’t ship a remediation workflow without giving admins the evidence and context they demanded. This ensured our MVP aligned with actual user behavior rather than idealized assumptions.
These collaborative workshop sessions achieved critical outcomes:
- alignment on core user journeys and user stories
- prioritization of features
- definition of success metrics
- clear scope boundaries for v1
A Pivotal Architectural Decision
Once user stories were defined through our cross-functional workshops, the design team held a focused co-design session to define the core experience and information architecture. As the team reviewed the distinct roles and workflows of the IAM and security teams, it became clear that the existing architecture wouldn’t support the structure the identity security product required. We faced a critical decision: Should we extend our existing design system and product structure, or create something new from scratch?
This wasn’t an easy choice. Our company’s existing product suite had been carefully designed for backup administrators—IT professionals focused on backup, recovery, and data retention. These users thought in terms of recovery points, backup schedules, and storage policies. IAM administrators, however, operate in a completely different mental space: They think about identities, permissions, risk scores, policy violations, and authentication methods.
We made a pivotal design decision to create a dedicated navigation space and design a framework separate from our existing product architecture.
A dedicated navigation space and design framework meant we would not be encumbered by design patterns optimized for a different persona. Instead, we could build purpose-built patterns that respected how IAM administrators actually think and work.
This wasn’t just an organizational choice; it was a strategic UX decision that
- respects the mental models of IAM admins who think differently about identity versus data protection;
- enables focused workflows without the cognitive overhead of unrelated features;
- supports independent purchasing decisions for organizations with different security priorities; and
- allows design differentiation unconstrained by existing patterns that don’t serve this use case.
The Identity Summary Page: Our Key Design Differentiator
The decision to rethink the architecture allowed us to truly innovate, keeping the user at the center. This allowed us to craft a comprehensive concept for an identity summary page.
The identity summary page is a holistic view of each identity across
- violations and alerts that are real-time security policy breaches;
- risk history over time from trending data showing risk trajectory;
- data access, specifically what sensitive information each identity can reach; and
- key attributes and authentication from identity metadata and authentication methods.
The comprehensive identity summary formed the centerpiece of our design differentiator. It earned quick, broad executive buy-in and widespread adoption among end users post-launch.
Phase 4: Design and Iteration (Weeks 8-14)
With tight timelines and high visibility, we entered an intense design sprint phase. We iterated quickly and discarded numerous early versions that didn’t meet the clarity or differentiation bar we had set. We benefited from cross-team collaboration, leveraging insights from colleagues who had worked in adjacent problem spaces.

Figure 1: Example of discarded design iterations.
Design Principles Guiding Our Work
Three core principles guided every design decision.
- Scalability: Build a foundation that scales from dozens to thousands of identities.
- Progressive disclosure: Show critical information first. Let users drill down as needed.
- Design differentiation: Create new patterns, not recycled interfaces.
Information Architecture
Rather than extending existing patterns, we created a new architecture centered on these aspects:
- risks, including violated policies, sorted by the riskiest identities
- alerts with actionable investigations requiring immediate attention
- policies with customizable detection rules
This structure aligned with user mental models and enabled faster decisions.
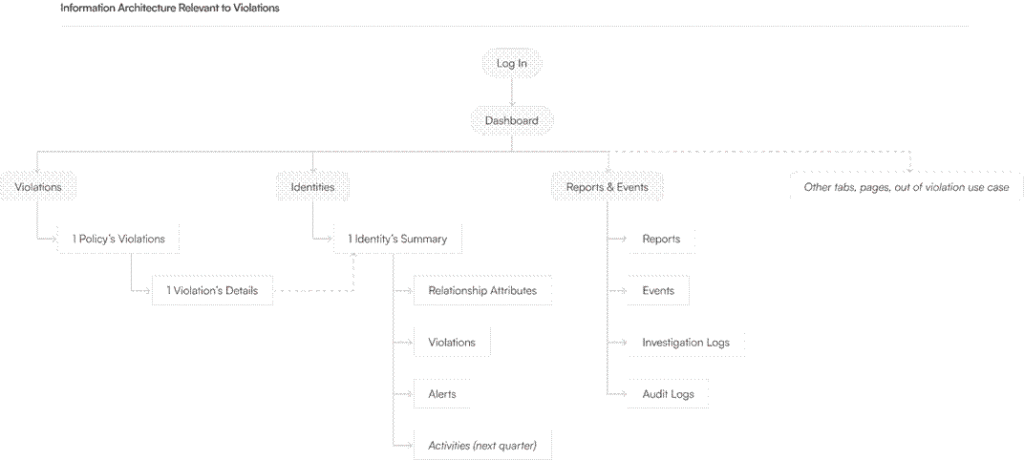
Figure 2: Information architecture for key workflows.
Validation Through Usability Testing
To validate our design decisions, we conducted rigorous usability testing with 12 real customers, including IAM admins and CISOs. Each 60-minute remote session focused on these defined user tasks:
- risk prioritization and remediation
- navigating the identity summary
- remediation workflow clarity
Table 4: Usability Testing Results
| Task | Success Rate | Key Insights |
| Identify the highest-risk identity. | 100% | Risk scoring was intuitive and clear. |
| Navigate to the identity summary. | 92% | The menu label needed refinement. |
| Understand violation details. | 83% | Context was needed earlier in the flow. |
| Initiate remediation workflow. | 75% | The confirmation dialog was unclear. |
| Review remediation impact. | 100% | Impact analysis is highly valued. |
| Filter identities by risk level. | 100% | Filtering was intuitive. |
Testing revealed one critical issue, four moderate issues, and one low-severity issue—all of which we resolved before launch. Feedback helped us fine-tune component clarity, navigational affordances, and critical information needed before taking action.
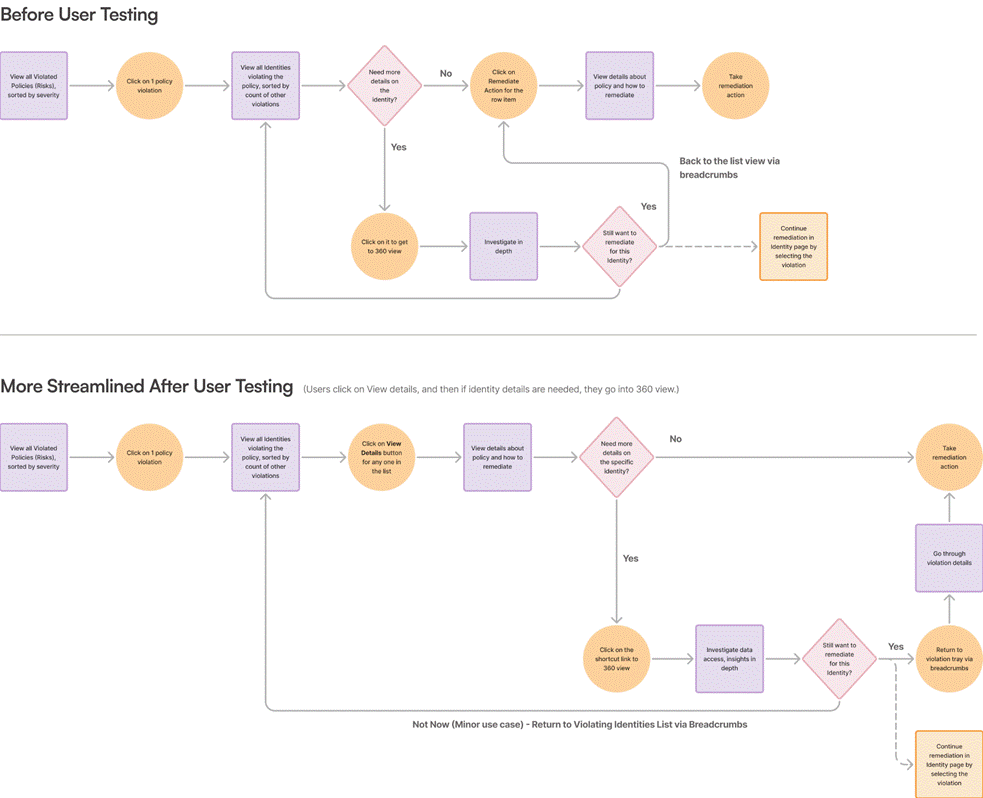
Figure 3: User flow before and after usability testing.
Phase 5: Delivery and Scoping (Weeks 16-20)
Strategic Prioritization
As development progressed and timelines became tighter, we knew that shipping a high-quality v1 experience would require strategic trade-offs. Rather than rushing to include every feature, we adopted a pragmatic delivery model that allowed us to focus on delivering the most critical value without compromising usability or coherence. We introduced a clear prioritization framework across the design artifacts by labeling each component (filters, columns, workflows, and micro-interactions) with P0, P1, or P2 designations. This helped cross-functional teams align on what was essential for the initial release and what could be safely deferred.

Figure 4: Priorities called out in the designs.
Precision in Onboarding
A critical success factor with any B2B enterprise product is designing the First-Time User Experience (FTUX) to accommodate different customer segments with varying levels of existing product familiarity. We designed four distinct onboarding flows.
Table 5: Segmented Onboarding Strategy
| Customer Segment | User Challenge | Onboarding Approach | Key Message |
| Existing Customers (Related Products) | Need to understand what’s new. | Highlight new capabilities and access paths. | “You’re already protected. Here’s what you can do now.” |
| Existing Customers (Core Products) | Need reassurance about existing configurations. | Clearly communicate there’s no changes to the current setup. | “Nothing changes. Explore new capabilities at your pace.” |
| Net New Customers (Partial License) | Need guidance without overwhelming complexity. | Lightweight flow focused on connecting the identity provider. | “Get started in three simple steps.” |
| Net New Customers (Full Suite) | Need comprehensive onboarding. | Sequenced onboarding prioritizes identity security. | “Let’s set up your complete security posture.” |
Across all user types, we designed the FTUX around a single clear action: Connect your first identity provider. From there, users could continue the setup process without opening Settings. Whether they needed to expand their configuration or add more providers, the experience stayed in-context, maintaining flow and clarity throughout.
This precision-focused onboarding strategy ensured that we
- protected existing configurations,
- accelerated time-to-value for new customers, and
- delivered a frictionless entry point into a complex product domain.
Final Designs and Outcomes
The final product represented a fundamental rethinking of identity security UX. At its core was our signature identity summary page. This holistic view unified previously fragmented information about violations, risk history, data access patterns, and authentication methods into a single, coherent interface. By creating a dedicated navigation space with purpose-built information architecture (flowing from risks to alerts to policies), we enabled IAM administrators to move seamlessly from strategic risk assessment to tactical remediation without the cognitive overhead of irrelevant features.
What made the outcome particularly gratifying wasn’t just the strong adoption rates or high satisfaction scores; it was the speed with which users internalized the new mental model. During post-launch feedback sessions, admins described feeling “in control” for the first time when managing identity risks, a qualitative signal that we had successfully transformed their workflow and their relationship to the problem.
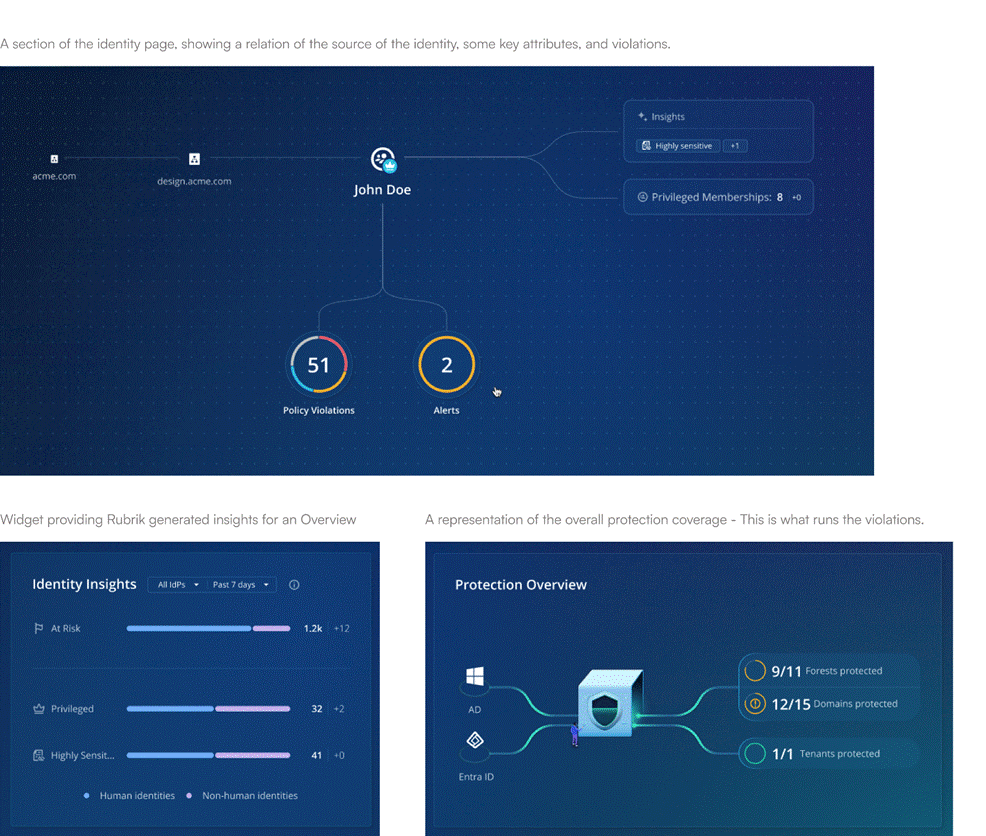
Figure 5: Key design concepts.
Key Lessons for 0-to-1 Product Design
- Research investment pays compound returns:
In high-stakes domains, grounding in foundational research isn’t optional; it’s essential. Our investment in understanding 15+ IAM admins and security professionals provided confidence in design decisions, clear prioritization criteria, compelling narratives for stakeholder buy-in, and reduced redesign risk in the process. The insights we uncovered became immutable truths that anchored every subsequent debate and trade-off.
- Workshop-driven alignment accelerates execution:
Our in-person workshops compressed weeks of potential misalignment into focused, collaborative sessions. The key was bringing the right people together with prepared materials and clear objectives. These intensive sessions created shared understanding and commitment that sustained the team through challenging trade-offs later in the process.
- Strategic architectural decisions create design freedom:
The choice to create a dedicated navigation space within the product was controversial but critical. It gave us flexibility to diverge from existing patterns when appropriate, optimize our specific user workflows, and create a distinct experience within the broader product suite. This decision exemplifies how strategic UX choices early in the process can unlock innovation downstream.
- Embedded prioritization enables speed with quality:
By labeling each component with P0, P1, or P2 designations directly in design artifacts, we eliminated ambiguity during implementation, preserved design coherence after scope reductions, created accountability across teams, and maintained design intent through development. This approach proved essential to shipping a polished v1 under tight timelines without compromising core user value.
- Precision in onboarding reduces friction and risk:
Our segmented onboarding approach recognized that existing customers had different needs than net new users. This precision built trust by protecting existing configurations, accelerating time-to-value for new users, reducing the support burden, and increasing adoption rates. In enterprise software, the onboarding experience often determines whether a product succeeds or fails. We designed four distinct experiences to ensure success across all customer types.
- Continuous validation reduces costly pivots:
Usability tests with 12 customers caught critical issues before launch. The IAM admins and CISOs revealed blind spots we’d missed internally. In high-stakes domains, the cost of post-launch pivots is exponentially higher than the investment in thorough pre-launch validation.
- Design must stay involved through delivery:
What distinguished our process was maintaining design involvement through final delivery. Too often, designers hand off specifications and disengage. We stayed deeply involved in scoping decisions, defended core experiences during de-scoping, and ensured engineering understood not just what to build, but why it mattered to users. This sustained engagement was critical to shipping a product that felt polished and coherent rather than compromised or fragmented.
Conclusion: Designing for Impact in High-Stakes Domains
Cybersecurity UX design requires a unique combination of precision, empathy, and systems thinking. In designing a new UI, we crafted a new framework for how admins perceive and act on risk.
This case study demonstrates that even in 0-to-1 situations with limited domain knowledge, tight timelines, and high-stakes consequences, rigorous research combined with collaborative design processes can yield exceptional outcomes. The key is maintaining unwavering focus on
- user needs over feature lists, so every design decision traces back to research insights;
- clarity over complexity as progressive disclosure prevents overwhelming users while supporting deep dives when needed;
- trust over novelty through earning user confidence with evidence-based design, clear impact analysis, and transparent workflows; and
- strategic trade-offs over scope creep through disciplined prioritization that enabled us to ship a polished v1 rather than an overdeveloped or compromised product.
We hope that this case study will empower other UX teams working in 0-to-1 spaces, especially within dense, high-risk domains. The principles and practices we employed—deep user research, strategic architectural decisions, continuous validation, embedded prioritization, and sustained design involvement—are transferable to any complex enterprise domain in which the stakes are high and the margin for error is slim.
In the end, designing for identity security taught us that, in high-stakes domains, every pixel, every word, and every interaction is a promise to users that we understand their challenges and have built something worthy of their trust. That’s the standard we held ourselves to, and that’s the standard we encourage other UX practitioners to embrace in their own challenging domains.
Acknowledgments
This work was made possible through collaboration across multiple teams. Special thanks to our design leadership, product design team, and user research colleagues for their contributions to usability testing, design feedback, and foundational explorations that informed this work. Their diverse perspectives and rigorous critique elevated the final product immeasurably.


User Experience Magazine › Forums › Beyond the Breach: Forging a Unique UX for Identity Security